- Dynatrace Community
- Ask
- Open Q&A
- High Severity cURL and libcurl CVE-2023-38545
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Oct 2023
02:39 PM
- last edited on
10 Oct 2023
03:11 PM
by
![]() Ana_Kuzmenchuk
Ana_Kuzmenchuk
High Severity for Curl en Libcurl CVE-2023-38545 has been brought to our attention.
Tomorrow news will come out about a high severity vulnerability for cURL and libcur. The advice is to conduct an analysis of where this vulnerability occurs.
https://www.rezilion.com/blog/cve-2023-38545-a-high-severity-curl-and-libcurl-cve-to-be-published-on...
This has not been posted yet at cve-status.dynatrace.com
Dynatrace CVE status (Common Vulnerabilities and Exposures) - Dynatrace Community
I have opened a Support ticket, as indicated on this page.
Solved! Go to Solution.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Oct 2023 02:54 PM
I have been following this and it seems that it is going to be at least a local execution exploit. You would probably have to be accessing a nasty site, so you then get exploited locally. Let's see what exactly what it is.
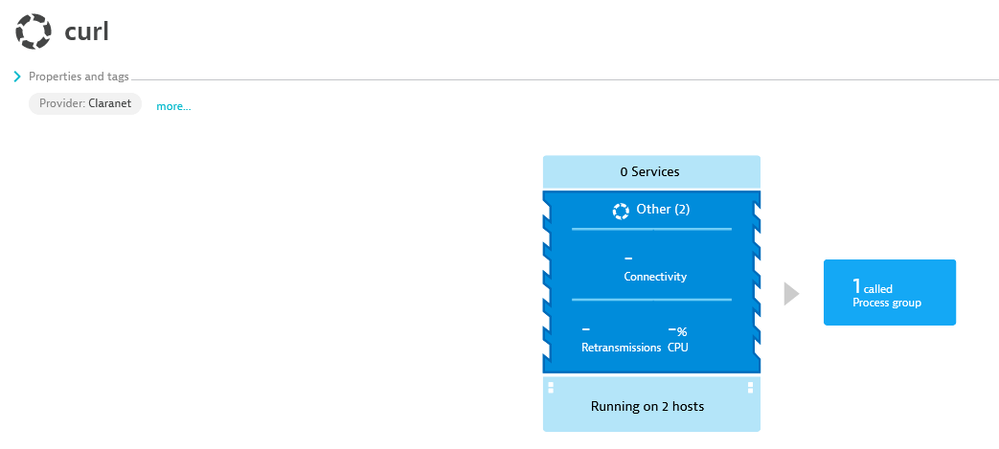
In the meantime, it's important to know if you have curl executing somewhere in your stack. Some of the curl executions might make it to the respective PG as below, but given that it normally executes for only a slight period of time, it might nor be automatically detetected by Dynatrace.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Oct 2023 03:27 PM
Thanks for the added info @AntonioSousa.
Curl can be found on all Linux boxes where also OneAgents, ActiveGates and Managed Cluster nodes are installed, and regularly utilized as tool in the life of an admin. And of course the Dynatrace admins are very trustworthy people, and will never use dodgy sites, But somehow the Security people are hard to convince 🙂 So I expect that they are persistent in havin the packages updated. I do not think that curl itself is a package that is part of Dynatrace and installed as such, in which case is will be a Linux admin matter.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Oct 2023 06:45 PM
I have checked if OneAgent & ActiveGate in some form use libcurl, but it doesn't seem to be the case. But eventually, some users might have scripts using curl (I have) that access Dynatrace (and other) API endpoints. I don't expect that to be a risk issue when we know about the vulnerability tomorrow, so let's wait 😉
- Mark as New
- Subscribe to RSS Feed
- Permalink
11 Oct 2023 12:57 PM - edited 11 Oct 2023 12:57 PM
Hi all, thank you for your patience. You can find our official response here
- Mark as New
- Subscribe to RSS Feed
- Permalink
11 Oct 2023 04:26 PM
IMHO, one more risk exaggeration, this time from the curl maintainer. For what I read of the vulnerability:
- curl has to be using a SOCKS5 proxy
- an attacker has to be able to point curl to a specific server they control
- curl is nor vulnerable in its default state, with the typical CURLOPT_BUFFERSIZE value
- latency & time replies are also involved
If you have like a public page that uses underlying curl , have changed the CURLOPT_BUFFERSIZE, have a SOCKS5 proxy (do you????), and it is slow, you might have a problem though!
Featured Posts