- Dynatrace Community
- Dynatrace
- Extend
- Extensions
- PostgresDB (remote monitoring) Extension 2.0 Question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
PostgresDB (remote monitoring) Extension 2.0 Question
- Mark as New
- Subscribe to RSS Feed
- Permalink
27 Apr 2024 12:07 AM
We are currently reviewing the new PostgresDB (remote monitoring) extension to see if we want to utilize this in our environment and take advantage of what it provides.
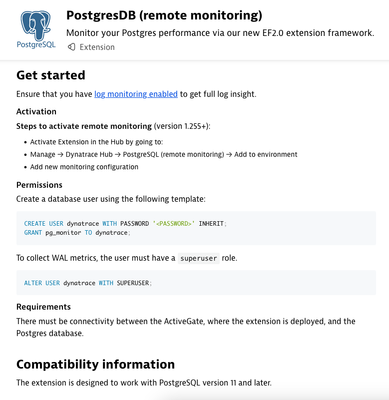
It mentions that the Dynatrace database user we need to create would need superuser role permissions in order to query/collect WAL metrics.
However, the concern is that the superuser role would technically have access to everything else the role inherently has access to.
As a company that follows a "least privilege" policy, is the superuser role required?
Could we not create a new role that only has SELECT access to the specific schemas/tables that Dynatrace needs to execute the WAL queries?
- Mark as New
- Subscribe to RSS Feed
- Permalink
29 Apr 2024 09:25 AM
This is as per Postgres documentation. Only a superuser can access the WAL metrics, this is not our decision but comes from postgres. Our database data source is unable to run any modifications by the way.
If it is still a problem, disable WAL metrics.
- Mark as New
- Subscribe to RSS Feed
- Permalink
29 Apr 2024 07:01 PM
Thank you for your response.
We want to view/use the WAL metrics.
We just don't want to make the Dynatrace user a superuser.
See Vagiz's response below.
- Mark as New
- Subscribe to RSS Feed
- Permalink
29 Apr 2024 10:40 AM
An alternative to using superuser would be to grant the pg_read_all_stats role to the user. Or, what is even more commonly done, is to grant the pg_monitor role.
Here is an excerpt from the Postgres v15 documentation:
The pg_monitor, pg_read_all_settings, pg_read_all_stats and pg_stat_scan_tables roles are intended to allow administrators to easily configure a role for the purpose of monitoring the database server. They grant a set of common privileges allowing the role to read various useful configuration settings, statistics and other system information normally restricted to superusers.
pg_monitor: Read/execute various monitoring views and functions. This role is a member of pg_read_all_settings, pg_read_all_stats and pg_stat_scan_tables.
We will look into updating the hub tile with the recommendation of using pg_monitor or pg_read_all_stats role.
- Mark as New
- Subscribe to RSS Feed
- Permalink
29 Apr 2024 06:58 PM
Thank you, Vagiz.
The current documentation states to grant the Dynatrace user the pg_monitor role.
Based on the PostgreSQL info you've shared, there is no need to grant the Dynatrace user the superuser role. Is this correct?
It looks like the only role the Dynatrace user needs is the pg_monitor role, which is already a member of the pg_read_all_stats role.
If this is the case, then this addresses our security concerns.
We just need the "Get started" documentation to be updated accordingly.
Thank you so much for your response.