- Dynatrace Community
- Ask
- Open Q&A
- SAML configuration for Dynatrace SaaS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
18 Sep 2019 08:38 AM
Hi Folks,
Can someone guide me how to set up SAML based authentication for dynatrace SaaS?
I went through the document link. There are several ways we can do it but we are not sure which way we should choose keeping in mind that it should not hamper default authentication.
Thanks...
Solved! Go to Solution.
- Mark as New
- Subscribe to RSS Feed
- Permalink
20 Sep 2019 08:46 AM
Hello,
1-go on sso setting and enter your domain and copy the value of txt registration.
2-add the txt registration on your dns zone
3-go back to setting and validate your domain, it should be ok
4-some others fields Will appear, download the first XML file and send it to you ad team and ask them to create a nex third party authentication on your adfs. Create some rules to transform attributes givenName, sn, groups.
5- asked ad team to generate for you the identity provider saml xml and upload it on dynatrace account/sso settings.
6-Configure the attributes
givenName, sn, groups
7-test communication with your adfs.
8-if not success check the doc, if OK, enable the sso and configure a dynatrace group which match with a attribute group on your ad.
Don't forget to use a local user (non member of your ad) during configuration steps! Have fun.
Regards aurelien.
- Mark as New
- Subscribe to RSS Feed
- Permalink
23 Sep 2019 12:21 PM
Thanks Aurelien for your comments.
Our environment uses Azure AD as IDP. Steps are given on portal but I'm not getting how we can manage the user permissions. Will it be on azure AD side or on dynatrace side?
If I assume it is on dynatrace side then, is it like we have to just update all already configured groups with ObjectId in the Security group claim name.
From where do I receive this object ID? Will this be a same object ID for all the groups?
Note:-We are using default authentication (dynatrace SaaS provided) and groups along with permissions are already configured.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
23 Sep 2019 03:13 PM
My recommendation about permissions management:
Creating dedicated Groups for your Dynatrace permission on your AD (example: Dynatrace_Readers, Dynatrace_Owners, Dynatrace_APP1_readers,...).
Add new groups on Dynatrace and specify the objectID of group previously created on Security group claim name fiels.
So you will be able to manage all permissions from your AD by adding users and groups on the dynatrace dedicated groups.
An other tip :
I have configured additional claim rules to get the list of AD Groups of current user and to send only the list of groups which the name begins with "DYNATRACE_" to http://schemas.xmlsoap.org/claims/Group attribute
With this tip I can use directly the name of AD group as Security group claim name on Dynatrace until the objectID.
On AD, add your personal account as member of dynatrace groups and be sure your SAML metadata are ok during SAML configuration validation :
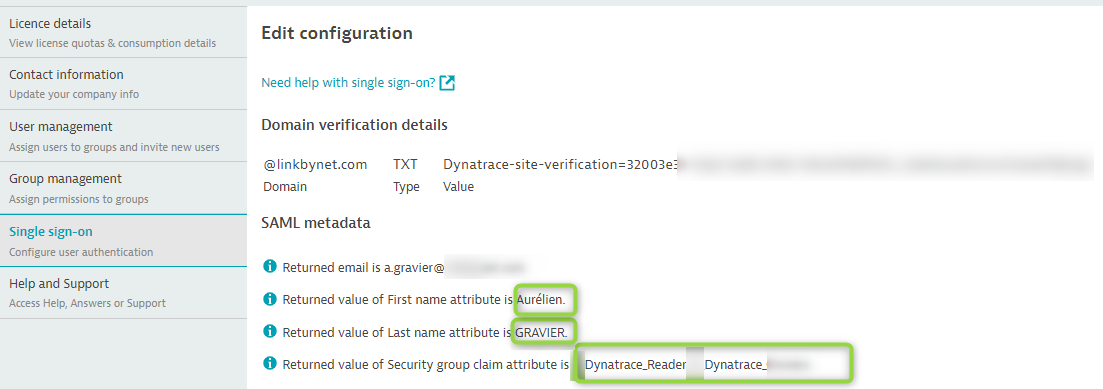
Hope it will help you.
- Mark as New
- Subscribe to RSS Feed
- Permalink
25 Sep 2019 12:04 PM
Hi Aurelien,
Thanks for you response.
Let me describe what we have done till now,
- We have created few Management zones on dynatrace SaaS under Settings --> Preferences --> Management zones
- Now under "Group management", groups are created with read-only, read-write access according to Management zones
- User are invited and assigned to these groups via "User management"
- User are now able to access the dynatrace environment using their own credential
I could see following approach for Azure AD integration,
- Delete user groups and users
- Follow the steps given in document for SSO integration to Azure AD
- Create a groups on Azure AD as suggested by you in previous comments
- Create a same group on dynatrace (copy the object ID from Azure AD) and assign Management zone to each group accordingly.
- Invite users and assign users to groups created on dynatrace (I assume this )
I assume that, above steps will give us the control over adding and removing users but group creation and deletion will be done on Azure AD side only.
Let me know if my understanding is correct.
Thanks...
- Mark as New
- Subscribe to RSS Feed
- Permalink
26 Sep 2019 10:55 AM
My comments in Bold below :
I could see following approach for Azure AD integration,
- Delete user groups and users : OK
- Follow the steps given in document for SSO integration to Azure AD : OK
- Create a groups on Azure AD as suggested by you in previous comments : OK
- Create a same group on dynatrace (copy the object ID from Azure AD) and assign Management zone to each group accordingly:
>> Name the group as you want on Dynatrace but the value of field "Security group claim name" has to exactly match with your Object ID (copy the object ID from Azure AD).
- Invite users and assign users to groups created on dynatrace (I assume this ) :
You don't need to invite users, just add them on the AD group
Regards.
- Mark as New
- Subscribe to RSS Feed
- Permalink
26 Sep 2019 03:15 PM
Hi Aurelien,
Thanks for your response.
I was wondering, by adopting this, we will loose control over application. We need to raise a request to AD team every time we need add any user.
Is there any way with which we can have control on dynatrace side for addition/deletion of users?
Thanks...
- Mark as New
- Subscribe to RSS Feed
- Permalink
26 Sep 2019 03:59 PM
You can continue to invite users if you want, don't worry !!
But, if you want to industrialize the process, I recommend asking to your AD team a delegation on a specific Active Directory Organizational Unit only with your Dynatrace resource groups with add/delete members permissions and sharing the mmc console to your team !
So you will be autonomous.
- Mark as New
- Subscribe to RSS Feed
- Permalink
14 Oct 2019 03:56 PM
Hi Aurelien,
How its gonna work if we continue to invite a users? because it will give link for user to set a password.
Thanks...
- Mark as New
- Subscribe to RSS Feed
- Permalink
14 Oct 2019 04:44 PM
The goal of SSO is to use the same account and password as you Active Directory so you have to manage your dynatrace permissions through your active directory groups.
When sso is enabled, you can invite users only for users who don't use email adress with the domain name configured on Dynatrace SSO feature.
Featured Posts
