- Dynatrace Community
- Ask
- Container platforms
- Re: Monitoring openshift: is it possible to monitor one project or namespace?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
17 Apr 2020 04:18 PM
Hi,
Customer is about to install Dynatrace to monitor Openshift 4.2. They are concerned about selective monitoring. I mean, is it possible to install it on a cluster, and only monitor processes/containers for an openshift project or namespace?
By default in Dynatrace you can disable a server that is the host for some layer (application servers of an specific application, for example). But in openshift, disabling a cluster node could mean disabling lots of entities for several projects, even the ones you want to monitor. How is this done? is an all or nothing thing?
Thanks in advance.
Antonio V.
Solved! Go to Solution.
- Labels:
-
openshift
- Mark as New
- Subscribe to RSS Feed
- Permalink
17 Apr 2020 05:05 PM
Of course it is possible now! It's done in container monitoring rules settings (Settings -> Process and containers -> Container monitoring):
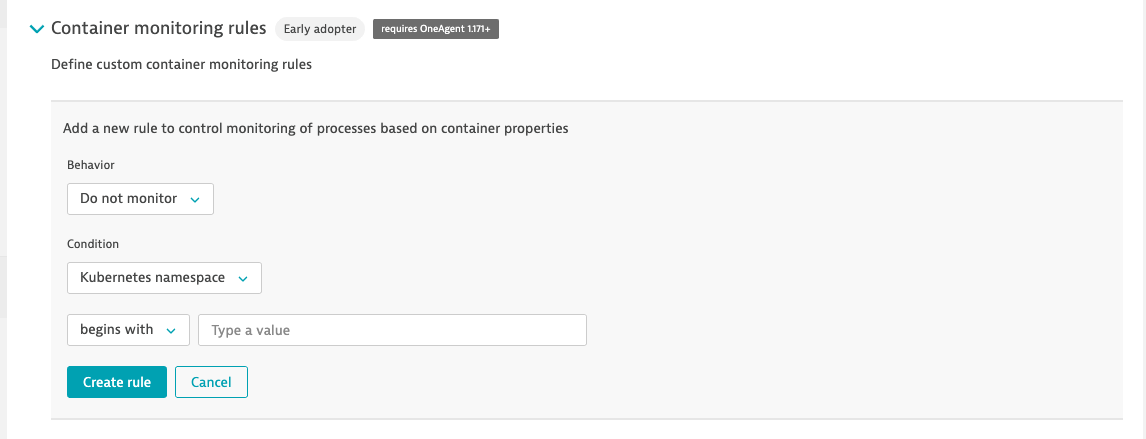
And you can filter events based on namespace as well:.
Dynatrace Managed expert
- Mark as New
- Subscribe to RSS Feed
- Permalink
17 Apr 2020 05:36 PM
Thank you very much.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11 Nov 2020 11:53 PM
Hi @Radoslaw S. sorry to bother. Quick question, is this possible to do via API? or via yaml at the moment of oneagent deployment? Or do it with a tag?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12 Nov 2020 09:17 AM
Not yet. Planned for CQ1/2021
Dynatrace Managed expert
- Mark as New
- Subscribe to RSS Feed
- Permalink
09 Jun 2021 10:03 AM
Hi @Radoslaw_Szulgo , the option via the yaml file, is this currently already available?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09 Jun 2021 02:28 PM
Yes, I believe this is in Environments v2 API : Settings -> look for the schema:
"schemaId": "builtin:container.built-in-monitoring-rule",
"displayName": "Built-in container monitoring rules",
looks like this at the moment:
{ "dynatrace": "1", "schemaId": "builtin:container.built-in-monitoring-rule", "displayName": "Built-in container monitoring rules", "description": "Dynatrace disables monitoring of containers that do not run any applications.", "documentation": "", "version": "0", "multiObject": false, "maxObjects": 1, "allowedScopes": [ "environment" ], "enums": {}, "types": {}, "properties": { "ignoreKubernetesPauseContainer": { "displayName": "Do not monitor containers where Kubernetes container name equals 'POD'", "description": "Disable monitoring of platform internal pause containers in Kubernetes and OpenShift.", "documentation": "", "type": "boolean", "nullable": false, "maxObjects": 1, "default": true }, "ignoreDockerPauseContainer": { "displayName": "Do not monitor containers where Docker stripped image name contains 'pause-amd64'", "description": "Disable monitoring of platform internal pause containers in Kubernetes and OpenShift.", "documentation": "", "type": "boolean", "nullable": false, "maxObjects": 1, "default": true }, "ignoreOpenShiftSdnNamespace": { "displayName": "Do not monitor containers where Kubernetes namespace equals 'openshift-sdn'", "description": "Disable monitoring of platform internal containers in the openshift-sdn namespace.", "documentation": "", "type": "boolean", "nullable": false, "maxObjects": 1, "default": true } }, "metadata": { "minAgentVersion": "1.171" } }
Dynatrace Managed expert
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jun 2021 08:46 AM
Hi @Radoslaw_Szulgo , this seems to be the API-way. Isn't it possible to configure this in the cr.yaml? Indicating the namespaces you want to monitor, so you don't need to create exclusion rules in the UI or via the API.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jun 2021 09:19 AM
I don't think this is support currently. Take a look at our Dynatrace operator (it's open-source):
https://github.com/Dynatrace/dynatrace-operator
Also I think that's a good idea for the Product to support this in the operator CR. Feel free to post it separately!
Dynatrace Managed expert
- Mark as New
- Subscribe to RSS Feed
- Permalink
12 Nov 2020 09:18 AM
You can open a product idea safely to keep the track of this.
Dynatrace Managed expert
- Mark as New
- Subscribe to RSS Feed
- Permalink
17 Apr 2020 05:20 PM
Hi Antonio,
It is possible to select which namespace you do and do not want to monitor in Dynatrace. You can find this in the Settings. Select Processes and containers and select Container monitoring.
There you will have the ability to modify the container monitoring rules to address the namespace you would or would not like to monitor.
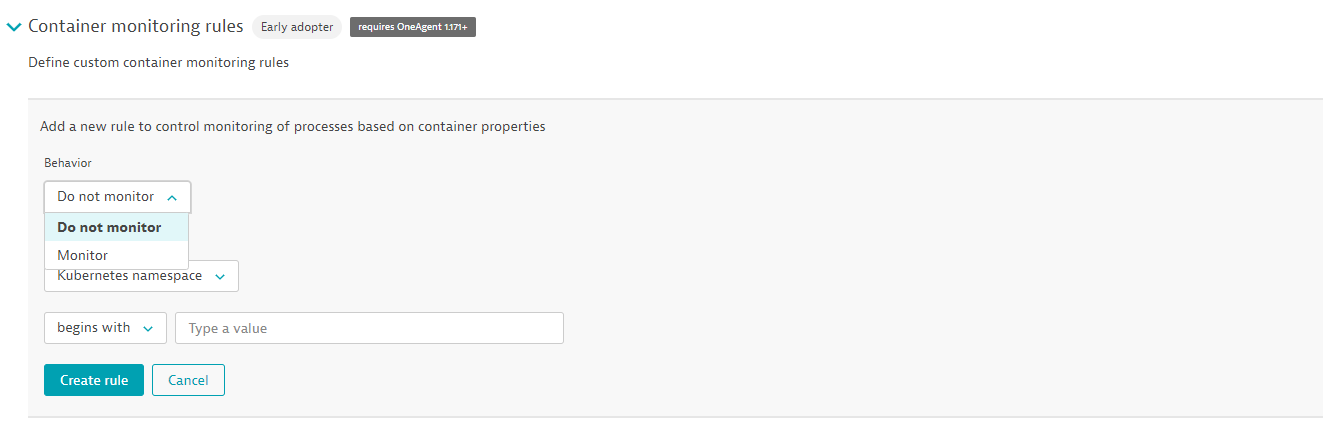
Best,
Sia
- Mark as New
- Subscribe to RSS Feed
- Permalink
17 Apr 2020 05:36 PM
Thank you very much.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02 Jun 2021 02:23 PM
Thank you for the information. Really helpful. But one question... Will this configuration (to limit the namespaces to monitor containers for) prevent the OneAgent from being injected in certain pods in Kubernetes?
My customer can't integrate Dynatrace to their K8s cluster currently, since its a share cluster so pods for two or three business units are run in the cluster. If they integrate to it (using the Dynatrace Operator) the OneAgent is spun up with their pods and that of the other business units, which depleats their HU license.
So if limiting the Namespaces for which Dynatrace should monitor containers, would this prevent the OneAgent from being deployed to containers for the other business units/systems?
Please advise
Francois
- Mark as New
- Subscribe to RSS Feed
- Permalink
09 Jun 2021 01:46 PM
Hi Francois,
Yes, this will address your use-case. Make sure that you create the exclusion rules before deploying the OneAgent operator. Create a 'do not monitor' rule for the other namespace/BUs.
Sia
Featured Posts
