- Dynatrace Community
- Ask
- Cloud platforms
- Re: Dynatrace SAAS SSO with Microsoft Azure - using claims/groups.link
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
20 Feb 2020
03:12 AM
- last edited on
15 Jan 2024
02:40 PM
by
![]() MaciejNeumann
MaciejNeumann
Microsoft Azure returns the group claim in the SAML using an attribute
http://schemas.microsoft.com/claims/groups.link
This happens when the number of groups is very high.
Can Dynatrace handle this scenario.
Eg (with groups.link): - Unable to do SSO with Dyantrace SAAS
<Attribute Name="http://schemas.microsoft.com/claims/groups.link">
<AttributeValue>
https://graph.windows.net/48d6943f-580e-40b1-a0e1-c07fa3707873/users/ba9b7081-e2a8-4427-9cdc-92afd7099833/getMemberObjects
</AttributeValue>
</Attribute>
I am able to successfully do SSO when the groups are returned as in identity/claims/groups, but not in the above scenario
Eg (with /claims/groups list) - This works for me
<AttributeName="http://schemas.microsoft.com/ws/2008/06/identity/claims/groups ">
<AttributeValue>a8c55d9b-fdc6-4fe3-9d56-af0f87419f2c</AttributeValue>
<AttributeValue>4604c7b6-57ca-4aa8-9a0b-235f4c9a3651</AttributeValue>
<AttributeValue>aa312f9f-c0ab-4e65-9bbb-07503792bdd8</AttributeValue>
Solved! Go to Solution.
- Labels:
-
azure
-
sso
-
user management
- Mark as New
- Subscribe to RSS Feed
- Permalink
20 Feb 2020 08:51 AM
According to this part of documentation:
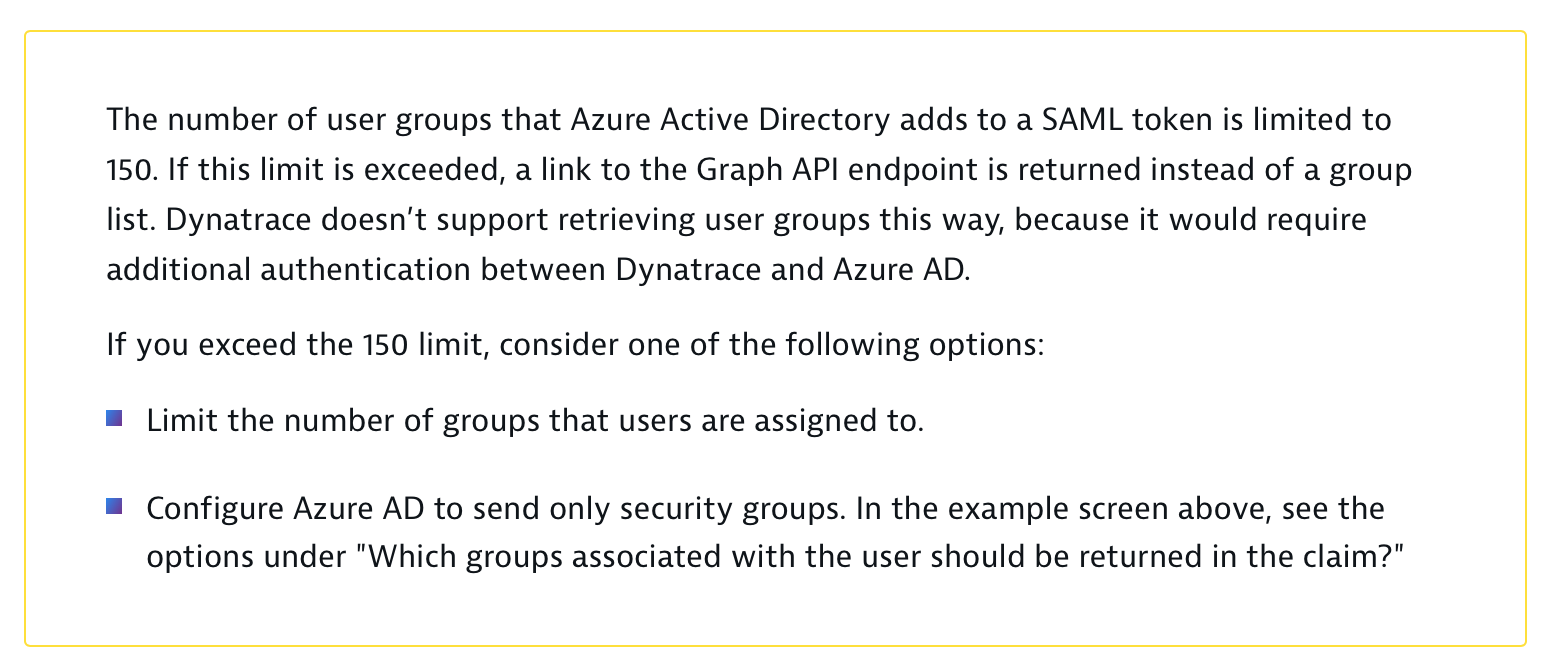
this will not work. https://www.dynatrace.com/support/help/how-to-use-dynatrace/user-management-and-sso/manage-users-and... You're limited to 150 groups.
Sebastian
- Mark as New
- Subscribe to RSS Feed
- Permalink
21 Feb 2020 12:33 AM
Thanks @Sebastian K.
From talking to Dynatrace, I think we have following two solution options. I am yet to try either of them, will share progress with the community.
- Configure Azure AD to send only security groups.
2. Use application roles rather than groups.
This limits the amount of information that needs to go into the token, is more secure, and separates user assignment from app configuration.
Change the Security group claim attribute. Something like this:
Before: http://schemas.microsoft.com/ws/2008/06/identity/claims/groups
After: http://schemas.microsoft.com/ws/2008/06/identity/claims/role
Featured Posts
