- Dynatrace Community
- Ask
- Extensions
- Re: Howto use tagging/alarm routing for certificate extension
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
18 Sep 2023
07:20 AM
- last edited on
18 Sep 2023
08:06 AM
by
![]() MaciejNeumann
MaciejNeumann
Does anybody have experience/suggestion how to route certificate alarms coming from cert extension (SSL Certificate Monitor | Dynatrace Hub)
I'm trying test and implement this extension which, after some applied fixes by Dynatrace, does what it should do. However I'm experiencing one big gap which support can't solve and suggesting an RFE which I can't imagine someone didn't solve it already.
The extension is detecting certificates on eg host and creates a custom device for each certificate. The extension is generating alarms once certificates are (going to be) expired. The problem is that I can't send these alarms to the right teams. I can't autotag these items eg based on the host they're detected on or the domain the certificate applies for.
Does anyone have experience with this and/or even solved this issue? I would have expected that via a entity selector rule using the relation or regex auto tag should be possible. Once autotagged the correct alarmprofile can be applied and alarms will be sent out to the right to solve the issue.
Looking forward seeing the responses,
Kind regards,
Daan
Solved! Go to Solution.
- Labels:
-
extensions
-
ssl
- Mark as New
- Subscribe to RSS Feed
- Permalink
19 Sep 2023 12:40 PM
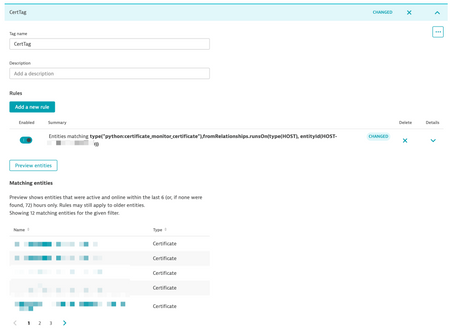
You can select all certificates related to a host with an entity selector like:
type("python:certificate_monitor_certificate"),fromRelationships.runsOn(type(HOST), entityId(HOST-xxxxxx))Apply this entity selector to an automatic tagging rule, you can get results like:
Would that solve your use-case?
- Mark as New
- Subscribe to RSS Feed
- Permalink
16 Oct 2023 01:42 PM
Due to holidays and stuff I didn't had the time yet to review this comment. Just tested it and it works like a charm! Only modification I've done rather than using a HostID I've been using the host tag based on the defined hostgroup.
- Mark as New
- Subscribe to RSS Feed
- Permalink
15 Jan 2024 06:11 PM
I have a similar situation, but I'm trying to have the certificates be recognized as belonging to a management zone, is there an entity selector I can set in the management zone rules that will accomplish this?
Thanks!
Featured Posts